
Email security is the multifaceted process of keeping email data and sensitive information protected by leveraging defensive techniques and technology. It all starts with education and knowing what to do and it's extremely important for businesses to keep their data exclusive to the owner of the account.
In today’s busy world, email is fundamental to communication. But what happens when something goes wrong and your security is compromised? Viruses, phishing scams, and information breaches are not uncommon and have high costs.
Email security is something that can often slip to the wayside, but it’s not complicated to put measures in place to avoid a messy situation. It’s incredibly important to be aware of the risks associated with using email and how to proactively protect against them to make sure that your data isn’t getting into the wrong hands.
The Cheat Sheet
Here’s a simple downloadable cheat sheet for you to print and make sure that your teams email accounts are kept safe and secure:

Want a direct link to this image for printing? Click here.
And now for a little more explanation…
1. Passwords
Passwords are one of the most important factors in keeping your email information safe. A good strong password is the first level of defense against a security breach.
Don’t use generic passwords. Things like CompanyName123 and FirstLastname! aren’t secure – especially when it comes to admin-level accounts. Here’s a nice little comic that we refer to make strong passwords for ourselves.
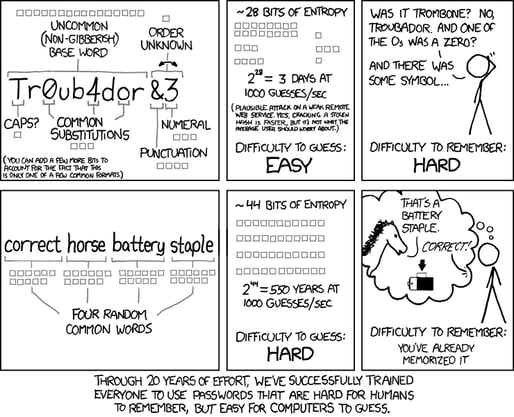
To make sure things stay secure, change your passwords often, and use different ones for each account. Also, make sure not to share passwords – even with members of your own team.
2. Spam
The first line of defense when it comes to spam is a strong spam filter. It seems self-explanatory, but it’s incredibly important to have a good filter in place to avoid having to interact with spam.
But, even with a filter in place, you should still exercise caution.
Never reply to spam or click any ‘unsubscribe’ links. This will just confirm to the spammer that your email address is legitimate.
3. Phishing
It’s important to learn how to recognize phishing emails because they can extract personal information and install malware on your system.
Phishing emails may contain threats to shut your account down, have poor grammar, and use words like ‘urgent’ to get you to give them sensitive information or click on a link that leads to a harmful download.
A reputable business will never ask for sensitive and personal information via email. If a message asks for things like passwords or social security numbers, this should put you on high alert.
Make sure to check the sender’s email address. Is it forged? Are there misspellings?
Do links in the email lead to a questionable source? At first glance, a link like yourbank.example.com might look like it leads to a page on yourbank.com, but it’s actually a completely different domain. A simple way to check the links is to hover over them to make sure they look legit before clicking on them.
It’s also a great idea to make sure that all sensitive data within your organization like credit card and social security numbers are stored on a private encrypted volume that has limited user access (perhaps only HR).
3. Attachments
Attachments are also another method to get access to your data. Before opening an attachment, make sure that you know who it’s from and that you are expecting it.
Save the large files (anything over 1 or 2 MB) for something other than emails like Google Drive or Dropbox.
Always make sure to scan all attachments with a good antivirus software program before opening and be especially aware of any zipped attachments, ones with unusual file types, and Office documents with macros. Scammers use all of these tactics to install malicious software on your machine.
4. Security
In addition to all of the above, general security measures can also be effective against malicious attempts.
Don’t send any personal information over email and make sure that your mail provider uses SSL or TLS to make sure that your email is encrypted from the time you hit the send button to when it shows up in the recipient’s mailbox.
Keep user drive permissions locked down and secure.
Even personal laptops that aren’t managed by your organization might already be infected and could even have networked drives mapped. Make sure that security software is up to date.
5. Educate
Email security doesn’t need to be complicated, but it’s one of those things that is necessary to talk about. The consequences can be drastic and are worth having a proactive plan against.
Education is the most important aspect of keeping your organization safe. Make sure everyone knows the above precautions and how to handle their email security.
Some other considerations…
Find My Phone
Ever use find my phone for your iPhone or Android? It’s especially helpful when you can’t remember if you left your phone in the car or not. Well, these same features enable you to remotely erase all your personal data, in the event your phone (or tablet) is lost or stolen. Make sure it’s enabled. It’s very easy to do so. Here’s how to do it on your iPhone and here’s how to do it on an Android phone.
Pop-ups
Pop-ups are pesky and super annoying -like, really annoying. However, they can also contain malicious software hidden in them that can trick a user into unknowingly verifying something. This could trigger a download unbeknownst to you and install malware. In most cases, do yourself a favor and avoid the tendency to “just click it”. If you think something looks suspicious, ask your IT specialist to check it out. Also, if you use the Chrome Browser on a Windows Machine, Google offers a free application that will “scan and remove software that may cause problems with Chrome, such as crashes, unusual startup pages or toolbars, unexpected ads you can’t get rid of, or otherwise changing your browsing experience.” Here’s the link.
Free Wifi?!
Enjoying your latte with a side of Free Wifi? Well, most Wifi hotspots at local establishments are not run by IT Professionals. This isn’t purposefully malicious, the owners are just trying to do you a solid and likely don’t realize one of their patrons is searching for data being transferred. In this case, once you’ve accessed the free Wifi, you’ve granted him/her free access to a program that can intercept your data. If you must use free Wifi, consider encryption software.
In the event your organization is in the process of evaluating security best practices or seeking a Managed IT Service provider, the folks at Ripple would welcome the chance to discuss where you are in the process. 
Don't Fall Behind!
Get the latest work-from-home and Humans First® IT tips straight to your inbox.
